We made it! This is the final post in this six-part series mapping the cybersecurity landscape through a new reference model for IT infrastructure security. Thank you for coming along on this journey with me. Now it’s time to take a look at where we’ve been, review the map itself, and discuss how to put it to work in your own environment.
We
started the series by reviewing some of the most popular and useful models and frameworks currently available. While all of these can serve as maps to help us build a secure infrastructure, they leave us with a couple fundamental questions unanswered:
Which tools provide defense in depth, and which are just causing duplication?
How do I compare competing products and the protections they provide?
To help answer those questions, we needed a clear way to map where individual security tools fit into a comprehensive security infrastructure. That’s where the reference model comes in, and the following four posts each zoomed in on each of the four domains of IT security:
- Perimeter - Network Security, Email Security, Web Security, DDoS Protection, Data Loss Prevention, and Ecosystem Risk Management
- Endpoint & Application - EPP / EDR, Patch & Vulnerability Management, Encryption, Secure Application Delivery, Mobile Device Management, and Cloud Governance
- Identity & Access - SSO (IAM), Privileged Account Management, Multi-Factor Authentication, CASB, Secure Access (VPN), and Network Access Control
- Visibility & Control - Automation & Orchestration, SIEM, UBA / UEBA, Device Management, Policy Management, and Threat Intelligence
Now we can zoom out and take a look at
the full picture:
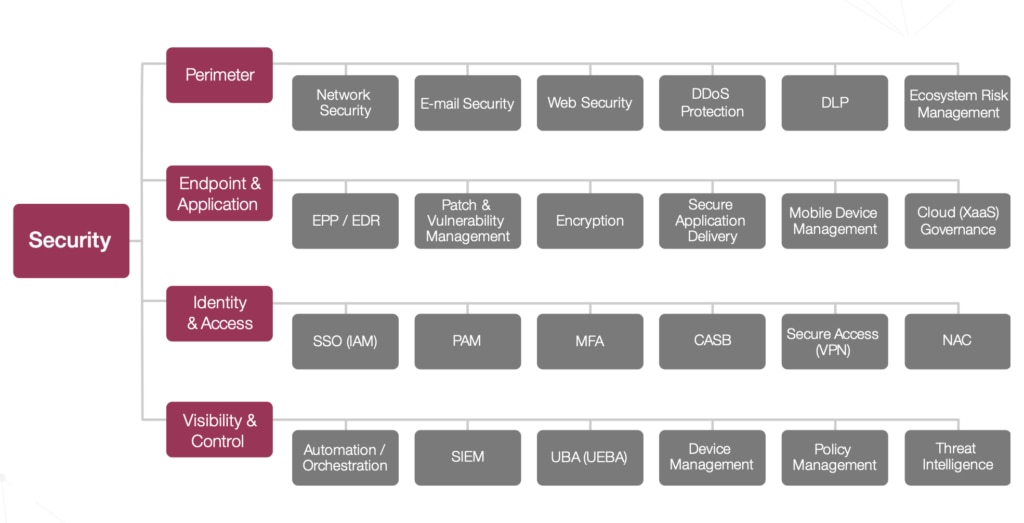
Think of this like one of the maps you might find in a mall or other public area, telling you confidently: you are here.
This particular map aims to give you the ability to answer those two stubborn questions above. By knowing which domain and category within the InfoSec landscape you are dealing with, you can evaluate various tools in an apples to apples comparisons. When the latest hot security company or product comes on the market, you can judge it against your existing infrastructure by placing it on this map.
How many network security devices, SSO services, or threat intelligence providers you need is unique to each organization. However, there is a big difference between intentionally adding depth to your security posture and unwittingly adding duplication. Use this model to ensure you only add the tools you really need, filling a gap or replacing a less adequate solution.
Speaking of gaps, that's another great way to use this map. There’s a third important question we can answer: Does your current security infrastructure provide the protection you need? Once you understand your organization’s risks and goals, you can use this model to ensure that all the right boxes are filled with a product or service that does the needed job.
Not every company needs a tool in each of these categories, of course, and some of you may need multiple protections in one or more of the categories. Also note that there are various ways to provide those protections. Each of these categories can be addressed by technical tools (hardware, software, and services), legal tools (e.g., contracts), organizational tools (policies and procedures), and human “tools” (like training and awareness), or a combination of two or more of these countermeasures. The key is understanding where real gaps exist, and what’s available to fill them.
Finally, we must always remember that the map is not the terrain. While I have found this model to be extremely useful in many discussions with CIOs, CISOs, IT management, and security practitioners, it can’t tell the whole picture. Thinking about the NIST Cybersecurity Framework of Identify, Protect, Detect, Respond, and Recover. This model sits mostly in the protect and detect realms. You still need talented staff or third parties to identify your most valuable assets, your compliance requirements, and your risks, goals, and vulnerabilities. Not to mention responding to attacks that do occur and recovering after an incident with policy updates, tool refreshes, or public relations.
Now it’s up to you – how will you use this new resource to better protect your organization?
 Think of this like one of the maps you might find in a mall or other public area, telling you confidently: you are here.
This particular map aims to give you the ability to answer those two stubborn questions above. By knowing which domain and category within the InfoSec landscape you are dealing with, you can evaluate various tools in an apples to apples comparisons. When the latest hot security company or product comes on the market, you can judge it against your existing infrastructure by placing it on this map.
How many network security devices, SSO services, or threat intelligence providers you need is unique to each organization. However, there is a big difference between intentionally adding depth to your security posture and unwittingly adding duplication. Use this model to ensure you only add the tools you really need, filling a gap or replacing a less adequate solution.
Speaking of gaps, that's another great way to use this map. There’s a third important question we can answer: Does your current security infrastructure provide the protection you need? Once you understand your organization’s risks and goals, you can use this model to ensure that all the right boxes are filled with a product or service that does the needed job.
Not every company needs a tool in each of these categories, of course, and some of you may need multiple protections in one or more of the categories. Also note that there are various ways to provide those protections. Each of these categories can be addressed by technical tools (hardware, software, and services), legal tools (e.g., contracts), organizational tools (policies and procedures), and human “tools” (like training and awareness), or a combination of two or more of these countermeasures. The key is understanding where real gaps exist, and what’s available to fill them.
Finally, we must always remember that the map is not the terrain. While I have found this model to be extremely useful in many discussions with CIOs, CISOs, IT management, and security practitioners, it can’t tell the whole picture. Thinking about the NIST Cybersecurity Framework of Identify, Protect, Detect, Respond, and Recover. This model sits mostly in the protect and detect realms. You still need talented staff or third parties to identify your most valuable assets, your compliance requirements, and your risks, goals, and vulnerabilities. Not to mention responding to attacks that do occur and recovering after an incident with policy updates, tool refreshes, or public relations.
Now it’s up to you – how will you use this new resource to better protect your organization?
Think of this like one of the maps you might find in a mall or other public area, telling you confidently: you are here.
This particular map aims to give you the ability to answer those two stubborn questions above. By knowing which domain and category within the InfoSec landscape you are dealing with, you can evaluate various tools in an apples to apples comparisons. When the latest hot security company or product comes on the market, you can judge it against your existing infrastructure by placing it on this map.
How many network security devices, SSO services, or threat intelligence providers you need is unique to each organization. However, there is a big difference between intentionally adding depth to your security posture and unwittingly adding duplication. Use this model to ensure you only add the tools you really need, filling a gap or replacing a less adequate solution.
Speaking of gaps, that's another great way to use this map. There’s a third important question we can answer: Does your current security infrastructure provide the protection you need? Once you understand your organization’s risks and goals, you can use this model to ensure that all the right boxes are filled with a product or service that does the needed job.
Not every company needs a tool in each of these categories, of course, and some of you may need multiple protections in one or more of the categories. Also note that there are various ways to provide those protections. Each of these categories can be addressed by technical tools (hardware, software, and services), legal tools (e.g., contracts), organizational tools (policies and procedures), and human “tools” (like training and awareness), or a combination of two or more of these countermeasures. The key is understanding where real gaps exist, and what’s available to fill them.
Finally, we must always remember that the map is not the terrain. While I have found this model to be extremely useful in many discussions with CIOs, CISOs, IT management, and security practitioners, it can’t tell the whole picture. Thinking about the NIST Cybersecurity Framework of Identify, Protect, Detect, Respond, and Recover. This model sits mostly in the protect and detect realms. You still need talented staff or third parties to identify your most valuable assets, your compliance requirements, and your risks, goals, and vulnerabilities. Not to mention responding to attacks that do occur and recovering after an incident with policy updates, tool refreshes, or public relations.
Now it’s up to you – how will you use this new resource to better protect your organization? 



