Access on the Source System
Understanding who has access to the system where the data originates is a great place to start —it's just not the whole story. You can pull the list of users who have access to the financial data through the financial application. This includes users who have access to create and view financial transactions and users who create and view reports. Too often, organizations stop there and provide that list as the answer. But there's more to think about, even just in the scope of the financial system. If your organization manages the financial application, you should also ask:- Who has access to the application database?
- Who has access to database backups?
- Who has access to the machine(s) on which the system is running?
- Does the system have functionality to automatically export reports? If so, where are reports exported to?
Downstream Systems
An organization's financial data can be useful for product managers, department managers, operations groups, and many other people. It's highly unlikely the data stopped at the financial system and its related reports. Your organization probably has a data warehouse and maybe some additional data marts. Now you need to get the list of users with access to those databases, including database and system administrators. And you need the list of users with access to the database backups from the data warehouse. Next, you find there’s a separate financial planning system, and your organization has a process to import data from the financial system to the planning system. Where the financial system was tied to AD users, the planning system doesn't integrate with AD. So now you need to link the planning application users to the actual people using those credentials. Your organization uses multiple reporting tools on top of your data warehouse. Let's say there’s a mix of Tableau, Power BI, and SQL Server Reporting Services. Users connect to the data warehouse using their AD credentials while building reports. But a service account is used to execute queries when datasets are refreshed or reports are run by these reporting applications. Now you need to go into each reporting application to get information on which users have access to the reports containing the financial information. Perhaps a single department adopted Tableau and used the local identity store rather than integrating with AD. Again, you need to determine who has access to the relevant reports and associate those users with people in the organization. And you need to identify administrators and those with access to database backups. Power BI grants access to reports and datasets in multiple ways. You can share an individual report, share an app, or grant access to a workspace. Access can also be granted to a dataset to allow users to build more reports with it. And Power BI has subscription capabilities where it can email an image of a report with a link to access the report. And there are ways to publish reports to the public internet. Luckily, Power BI uses Azure Active Directory for authentication and has PowerShell commands to help gather permissions information. You also need to consider people who exported reports and put them in SharePoint for the big quarterly financial meeting. Reporting Services is used mostly for tabular reports exported to SharePoint. Now you need to identify which SharePoint libraries contain financial data and who has access to them.It Gets Complicated
This example, illustrated in Figure 1, could be from almost any mid-size to large organization. In larger organizations with more systems and file stores and data repositories, it’s much more complicated.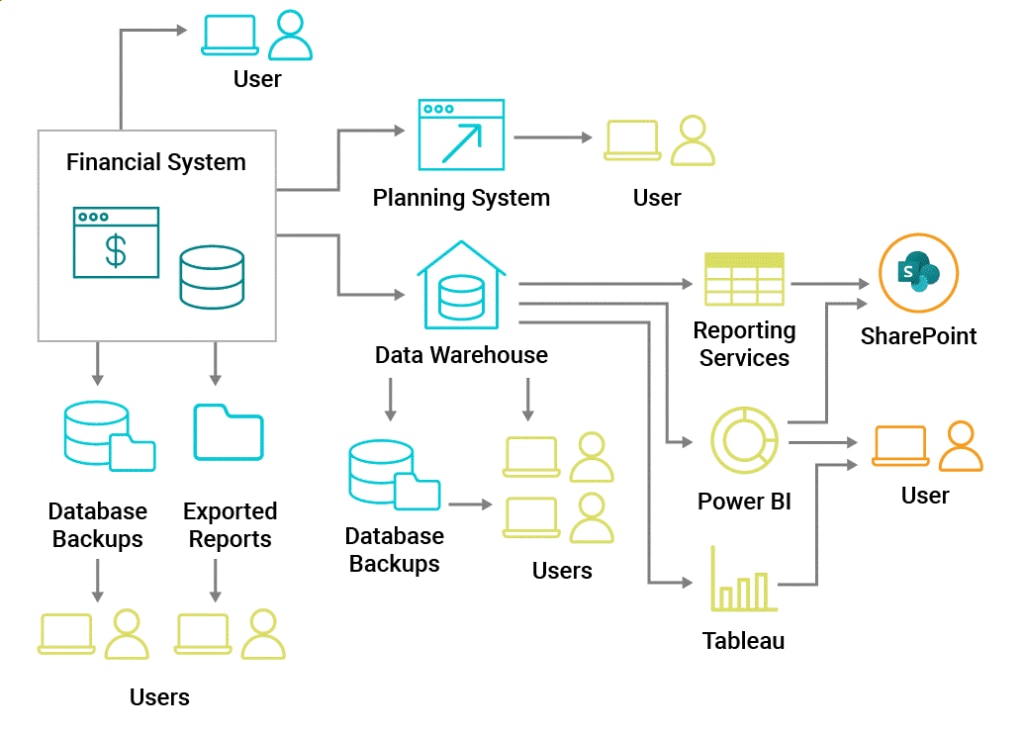
Figure 1: Financial data flowing from the original system throughout the organization
It illustrates why it’s so important to take a proactive approach to access control management. Access control management isn't just a technology—it requires people and process— but technologies that assist in access control management across the silos of individual systems can play a critical role. Access should be regularly audited for both regulatory compliance and organizational security. Without an overarching strategy on access control and how it integrates with identity management and each application your organization adopts, your organization is exposed to unnecessary data security risks. There are legitimate business reasons why those users needed the data, but everyone needs to play their part in appropriately handling sensitive data.