Determining and Refining Your Scope of Visibility
What needs to be included in the scope of your monitoring strategy? This commonly asked question requires a balanced effort of diligence and detective work. Determining the scope of IT monitoring activities must start with creating an outline of relevant systems information from all of your platforms. This will allow for the individual aspects of each system to be delivered and broken down by their appropriate stakeholders for deeper levels of evaluation. Taking the outline and collaborating with all IT groups in the organization will help you define and implement monitoring with complete visibility into the IT assets you have. This will include looking at specialized hardware devices and cloud-based networks being used, as well as the traffic routes throughout all systems, including hybrid cloud configurations. But as helpful as this is, the potential for systems to still remain hidden may require the use of monitoring tools to aid in their discovery.The Illusion of Comprehensive Monitoring Coverage
Having all the top-notch, award-winning monitoring tools at your disposal won’t be enough to ensure comprehensive monitoring coverage. Many monitoring tools can create the illusion of seeing everything of note within your infrastructure, but it only create a false sense of security. This is especially noticeable when data packets containing sensitive information disappear from view for periods of time, appearing as if by magic within another system on your network. This is a solid indication of a monitoring blind spot. This indication alone should shed some light into the capabilities of your current monitoring tools. It may be tempting to throw more tools at the problem, but this just leads to monitoring sprawl that does nothing to alleviate the false sense of security you once enjoyed. So now what? What type of monitoring tools work best to provide a true sense of security through the elimination of network blind spots?Uncovering Your Infrastructure Skeletons
Clarity is the essence of a successful IT department. Security protocols and configurations must be crystal clear, as does the knowledge of what servers are hosting which application. You must also be aware of the status of every asset in the organization. Gaining clarity into the root cause of the Hows and Whys behind system blind spots will help remediate these systems and bring them back into compliance with your organization’s specifications. You must have the right tools in place to perform the advanced levels of root cause analysis necessary for peeling away the layers of your network onion. The monitoring tools used to uncover hidden IT assets must, at the most fundamental level, provide the ability to bring together the complex layers of monitoring data from multiple platforms to succeed in these efforts. Also, the monitoring solution must employ intuitive levels of machine learning (ML) to help uncover hidden IT assets. Utilizing ML-based monitoring tools reduces the time spent executing root cause analyses while putting together a complete picture of your IT assets. ML will also be an invaluable aid toward eliminating monitoring silos have a tendency to devolve into time-consuming manual tasks for IT administrators.Eliminating the Visibility Gap With Single-Pane-of-Glass Monitoring Solutions
Identifying the stray pieces of technology in your stack and centralizing them (see Figure 1) for effective monitoring and management is an achievable goal. Single-pane-of-glass monitoring configurations give you an edge, thanks to their ability to present data from multiple infrastructure sources and present them in one, unified, view. These configurations provide a one-stop view into the inner workings of a network and help identify stray IT assets that need to be brought back into the fold.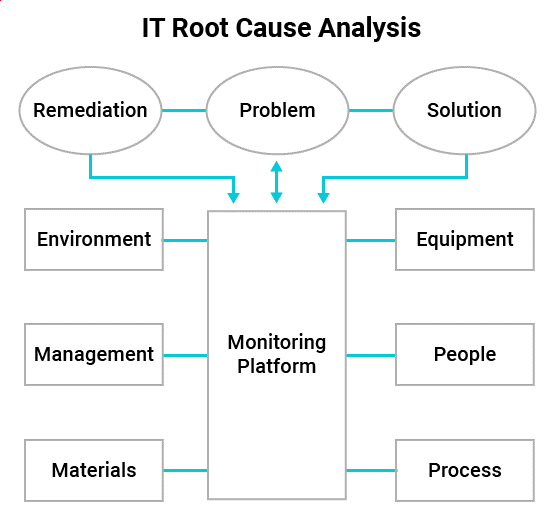
Figure 1: Example of monitoring tools managing all assets
This type of monitoring solution possesses the ability to operate effectively in the complex and fast-paced IT environments of today while providing concisely targeted task automations that deliver true comprehensive monitoring coverage across your IT assets. It’s also agnostic in its ability to integrate within systems, and provides automated escalation actions, as well as advanced remediation actions as required—all within one innovative tool.





