The Mossack Fonesca “Panama Papers” hack is the latest security breach to drive home how much an impact an SQL injection can have on modern-day organizations. Though that hack ultimately revealed massive professional fraud by companies and governments around the world, it involved the exposure of 11.5 million confidential documents. The 2.6 terabytes of data stolen were a powerful reminder that the history of web-based business has been riddled with instances of SQL injections. They remain common and potentially devastating to organizations.
Other high-profile examples of SQL injection include an instance when NASA sites were hacked in 2009, yielding site administrator info; when Heartland Payment systems were rummaged in 2008, resulting in the exposure of 134 million credit cards; and earlier this year, when the high-profile Ashley Madison leak occurred, many experts’ first thought was “SQL injection” (though that was later stated not to be the case). In 2012, Neira Jones, the head of payment security at Barclaycard cited SQL injections as responsible for 97 percent of all data breaches. And the Open Web Application Security Project called SQL injections the number one most prevalent attack in 2013.
The abundance and risk of SQL injection means that it’s vital for businesses to be able to detect when their own systems have been targeted, so they can respond as quickly and tactically as possible.
In the past, just knowing that your databases were under attack was difficult. However, SolarWinds® Database Performance Monitor (DPM) includes basic SQL injection detection for MySQL out of the box, ensuring that security teams, database administrators, and even CTOs can be made aware at the first sign of an attack. With our new Alerting & Integration module, those injection warnings can be transmitted directly to email, Slack, Victorops or any number of other messaging systems. We’ve written about our methods for detecting SQL injection in prior posts. As we mentioned there, we've actually built our SQL injection detection as part of our Query Analysis feature, so you can view the results of our detection as part of the Query Analysis dashboard. We class SQL injection events as “critical.”
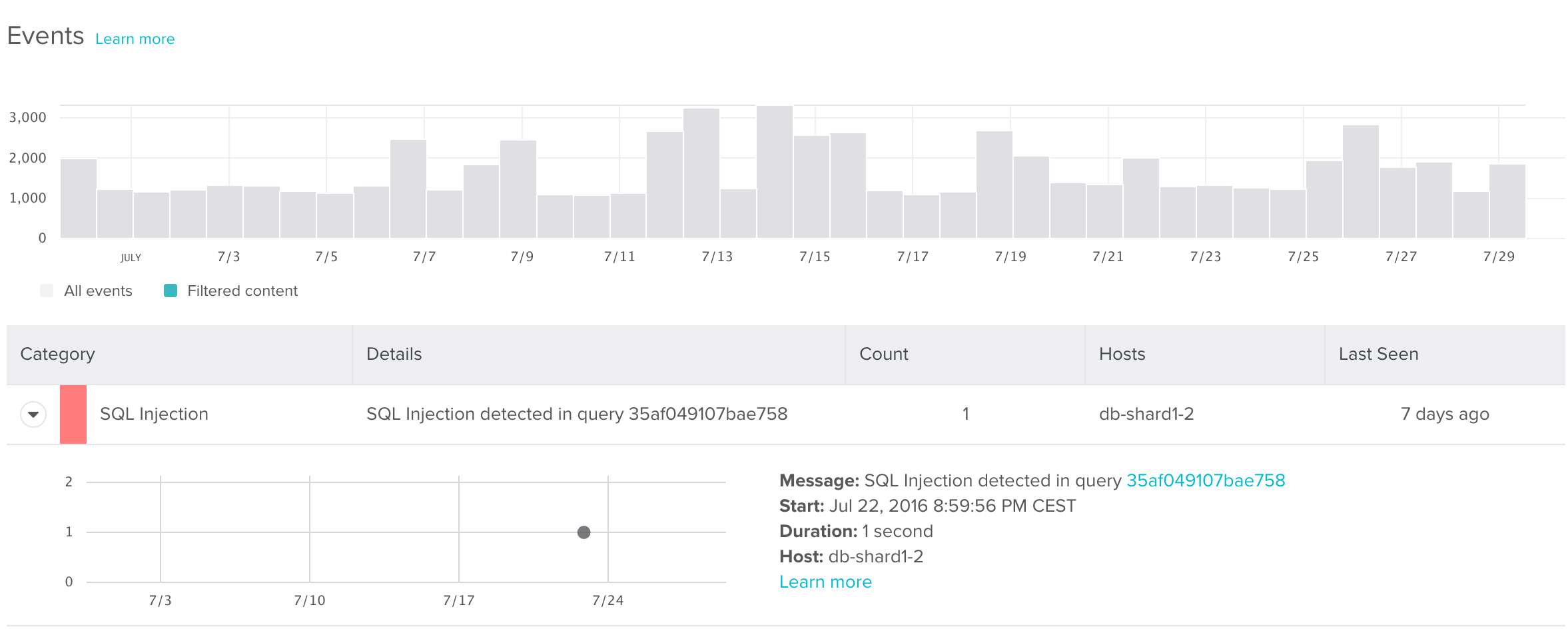
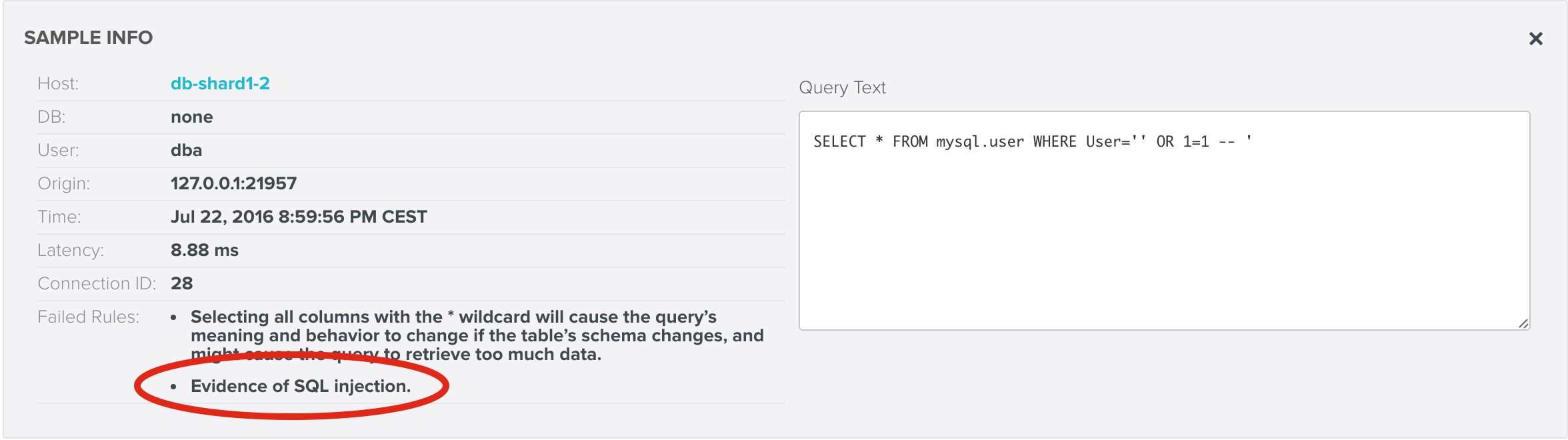 [In Sample Info, if "Failed Rules" reads "Evidence of SQL injection" as it does here, you'll know you need to take action.]
[In Sample Info, if "Failed Rules" reads "Evidence of SQL injection" as it does here, you'll know you need to take action.]
This is the first Database APM platform to reveal potential threats with such precision and speed. This can be used as a powerful, proactive, preventative measure: though many unskilled attackers will be able to trigger injections, they most likely will be unable to exploit them. However, the moment a skilled hacker is the one doing the probing, you're totlled. Knowing that, if you watch your system vigilantly, with the help of SolarWinds DPM. hopefully the frequent-but-unskilled probes will bring prompt attention to the faulty components that use unsanitized inputs.
If you want to see SolarWinds DPM in action, you can get a
free trial now.

 [In Sample Info, if "Failed Rules" reads "Evidence of SQL injection" as it does here, you'll know you need to take action.]
This is the first Database APM platform to reveal potential threats with such precision and speed. This can be used as a powerful, proactive, preventative measure: though many unskilled attackers will be able to trigger injections, they most likely will be unable to exploit them. However, the moment a skilled hacker is the one doing the probing, you're totlled. Knowing that, if you watch your system vigilantly, with the help of SolarWinds DPM. hopefully the frequent-but-unskilled probes will bring prompt attention to the faulty components that use unsanitized inputs.
If you want to see SolarWinds DPM in action, you can get a free trial now.
[In Sample Info, if "Failed Rules" reads "Evidence of SQL injection" as it does here, you'll know you need to take action.]
This is the first Database APM platform to reveal potential threats with such precision and speed. This can be used as a powerful, proactive, preventative measure: though many unskilled attackers will be able to trigger injections, they most likely will be unable to exploit them. However, the moment a skilled hacker is the one doing the probing, you're totlled. Knowing that, if you watch your system vigilantly, with the help of SolarWinds DPM. hopefully the frequent-but-unskilled probes will bring prompt attention to the faulty components that use unsanitized inputs.
If you want to see SolarWinds DPM in action, you can get a free trial now. 


