USER and PASSWORD and verifies they match using the following query, PHP/MySQL:
$isValidUserQuery = "SELECT 1 FROM users WHERE nick='" . $USER . "' AND pass='" . $PASSWORD . "'";
An attacker may try using
' OR 1=1 --
USER. The resulting $isValidUserQuery is:
SELECT 1 FROM users WHERE nick='' OR 1=1 -- ' AND pass=''
1=1 is always true, so user is considered valid! Because the system's sanitation and validation are sloppy, a simplistic workaround lets an intruder gain access to the system! So, If you have unsanitized inputs, your web app, site, or other sensitive destination is easily accessible to those whom you'd much rather keep out. And once they're in, the intruder may be able to fetch, modify and destroy data.
Unfortunately, such attacks and attackers are not rare. Any public-facing site or web app is probed for unsanitized inputs rather frequently by unskilled individuals. A study in 2012 reported, “Most web applications receive 4 or more web attack campaigns per month” while “some websites are constantly under attack.” In one case, the study observed that over the course of 180 days, one website was under attack 98% of the time. Fortunately, though unskilled attackers will be able to trigger injections, they most likely will be unable to exploit them.
However, the moment a skilled hacker is the one doing the probing, you're totaled. Knowing that, hopefully the frequent-but-unskilled probes will bring prompt attention to the faulty components that use unsanitized inputs.
With Database Performance Monitor (DPM), we've actually built our SQL injection detection as part of our Query Analysis feature, and you can view the results of the detection as part of the Query Analysis dashboard.
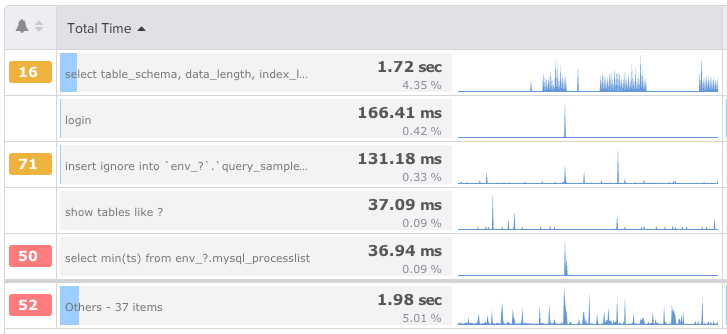
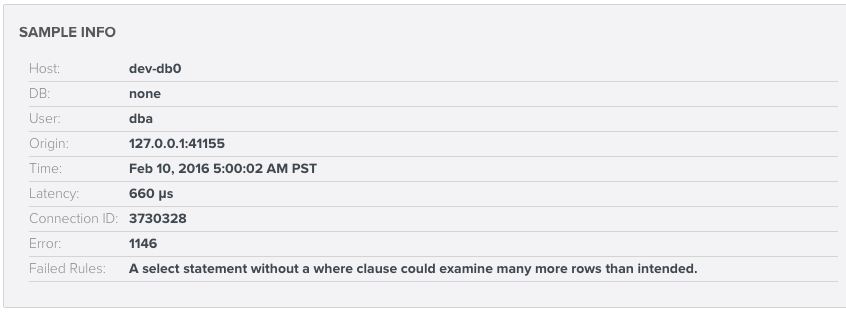 In Sample Info, if "Failed Rules" reads "Evidence of SQL injection," you'll know you need to take action.
The detector behaves according to a powerful rule, and customers have already benefitted from its efficacy. (We won’t detail the rule here, publicly, for obvious reasons.) Such a rule detects the simplest and most common case of injection, and as we gather more information, it will set a strong basis for adding further rules in the future.
We hope that if you have any questions about how DPM handles data security or about the systems we've put in place to protect our systems, you won't hesitate to ask.
In Sample Info, if "Failed Rules" reads "Evidence of SQL injection," you'll know you need to take action.
The detector behaves according to a powerful rule, and customers have already benefitted from its efficacy. (We won’t detail the rule here, publicly, for obvious reasons.) Such a rule detects the simplest and most common case of injection, and as we gather more information, it will set a strong basis for adding further rules in the future.
We hope that if you have any questions about how DPM handles data security or about the systems we've put in place to protect our systems, you won't hesitate to ask. 






