Most of us have no idea if our credentials are out in the wild, for bad actors to take and use for malicious intent. Unfortunately, they often are. Since October 8, 2019, research from SpyCloud—our partner in delivering Identity Monitor—has uncovered over 630 million additional plaintext credentials from the criminal underground. These have been added to the database powering Identity Monitor, which now checks user accounts against nearly 21 billion passwords to see if you’re vulnerable to a breach.
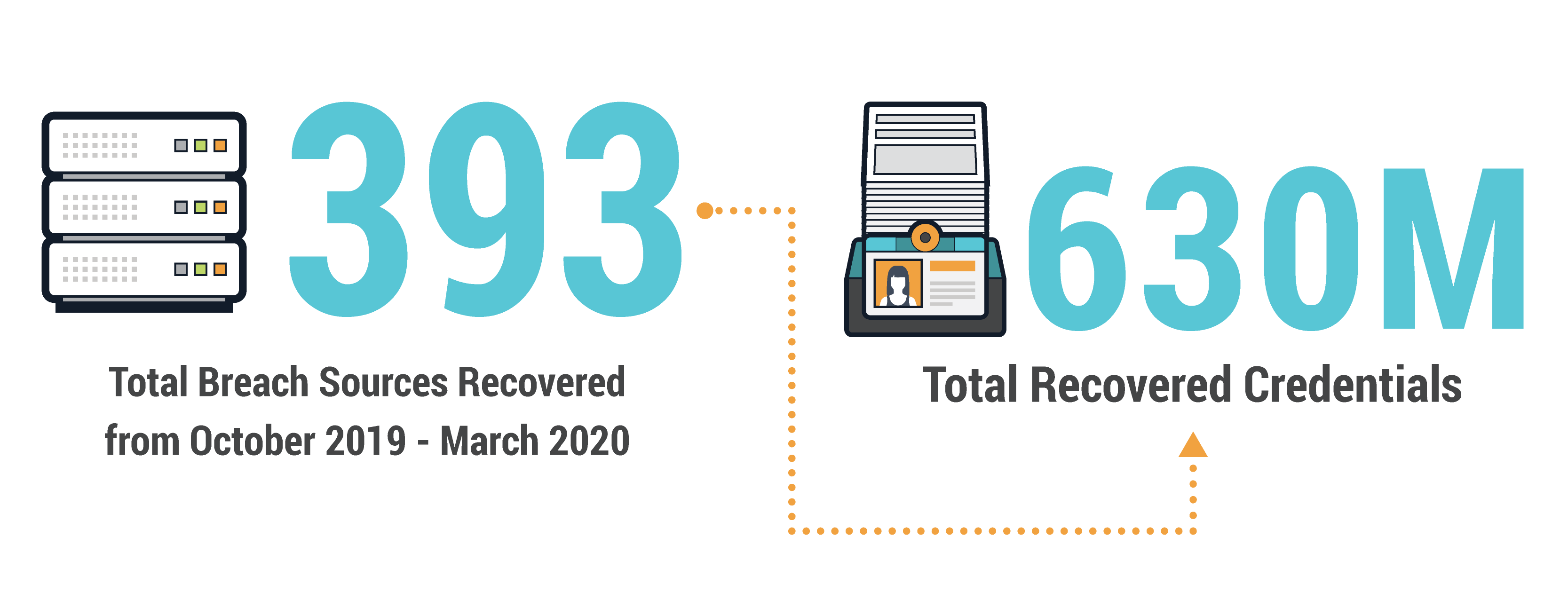
New breaches happen all the time, enabling cybercriminals to use freshly stolen passwords to take over any account sharing the same login details. In the past six months, over 393 total sources have been discovered by researchers who use human intelligence to infiltrate criminal communities and recover stolen credentials as soon as possible after a breach.
With more and more users working from home due to the COVID-19 pandemic, it’s more important than ever to ensure employee accounts are secured by unique passwords that haven’t been exposed on the criminal underground. If an employee reuses their work credentials on another site subject to a data breach, criminals are just one step away from breaching your organization.
Recovered Credentials Reveal Weak Password Choices
The credentials collected since October show a common pattern: People often choose weak passwords. Within the dataset, the passwords “123456” and “123456789” each appeared over a million times. Many other common passwords, such as “password,” “qwerty,” and “123123” appeared hundreds of thousands of times.
Many businesses think their employees are safe from this mistake because of strict password complexity requirements. However, these types of requirements can encourage bad behavior, as users struggle to remember complex passwords. Criminals know users frequently “update” a favorite password to meet requirements by adding a few digits at the end (Password1!) or replacing certain characters with similar-looking numbers or symbols. Case in point: “P@ssw0rd” appeared 15,244 times within the dataset. Sophisticated crimeware makes it easy for criminals to check for matches using these common variations at scale. An employee who uses the same password everywhere also poses a high risk, even if the password technically follows corporate requirements.

Outdated Password Hashing Methods Dominate
Organizations typically hash stored passwords to protect them in case of a data breach. Unfortunately, many common hashing methods are now considered outdated. Methods such as unsalted md5 and sha1 can be cracked easily and quickly, enabling criminals to use plaintext passwords in
account takeover attacks.
Unfortunately, many of the credentials recovered since October were hashed using outdated algorithms. For example, a staggering 66% were hashed with sha1.

Stolen PII Puts Businesses and Users at Additional Risk
Data breaches expose more than login credentials. Beyond emails, usernames, and passwords, researchers have collected 4.22 billion additional breach assets over the last six months—personally identifiable information (PII) and account information that can enable criminals to impersonate employees, bypass multi-factor authentication, or otherwise take over employee accounts.
For example, in the last six months, over 12.8 million bank numbers, 10.8 million Social Security numbers, 13.7 million national ID numbers, and other information criminals can use for identity theft and financial fraud were uncovered. Even seemingly innocuous data, such as social media usernames and job titles, can facilitate
business email compromise.
Here’s a subset of the personally identifiable information (PII) collected:

Conclusion: Stay Vigilant
Data breaches aren’t going to stop, and some signs even point to an uptick during the global pandemic. Examining what information is part of recent breaches can give you some insight of areas where you may be vulnerable. It’s a good time to revisit your password policy, and ensure you’re guiding your employees towards safe behavior.
Suggested next step: if you haven’t already, check your account takeover exposure. See if information associated with your email is already a part of our database of recovered stolen credentials.
 New breaches happen all the time, enabling cybercriminals to use freshly stolen passwords to take over any account sharing the same login details. In the past six months, over 393 total sources have been discovered by researchers who use human intelligence to infiltrate criminal communities and recover stolen credentials as soon as possible after a breach.
With more and more users working from home due to the COVID-19 pandemic, it’s more important than ever to ensure employee accounts are secured by unique passwords that haven’t been exposed on the criminal underground. If an employee reuses their work credentials on another site subject to a data breach, criminals are just one step away from breaching your organization.
New breaches happen all the time, enabling cybercriminals to use freshly stolen passwords to take over any account sharing the same login details. In the past six months, over 393 total sources have been discovered by researchers who use human intelligence to infiltrate criminal communities and recover stolen credentials as soon as possible after a breach.
With more and more users working from home due to the COVID-19 pandemic, it’s more important than ever to ensure employee accounts are secured by unique passwords that haven’t been exposed on the criminal underground. If an employee reuses their work credentials on another site subject to a data breach, criminals are just one step away from breaching your organization.











