Our hybrid world is rapidly growing and changing due to emerging technologies like artificial intelligence (AI), machine learning (ML), robotics, quantum computing, and cloud services. While these advancements bring many advantages, they’ve also made digital systems more complex, increased cost, and introduced new cybersecurity challenges.
The growing dependence on digital technologies, interconnected networks, and the vast volume of data generated has established a fertile environment for cybercriminals to exploit vulnerabilities. In today’s world, cybersecurity threats have moved from the occasional online hack and identity theft to become more frequent and sophisticated as cybercriminals continually refine their techniques and tactics to achieve various objectives, like accessing, changing, or destroying sensitive data/information through phishing attacks, blackmailing users via ransomware attacks, and other types of cyberattacks designed to disrupt business continuity.
In this post, I will explain the role of new technology in generating vulnerabilities and the importance of safeguarding sensitive information with an effective cybersecurity strategy. Given the constant evolution of threats, I'll explore the need to protect personal data, customer information, financial records, and intellectual property from unauthorized access, theft, and malicious activities. Additionally, I will provide guidance on how you can assess your existing cybersecurity measures with emphasis on the vital role of security solutions in preserving the security of your environment today and in the future.
How new technologies can introduce new vulnerabilities
As technology advances rapidly, information security and cybersecurity professionals often need help keeping up with emerging threats and implementing robust security measures promptly. Any delay in addressing security concerns can create a vulnerable period during which cybercriminals can exploit weaknesses.
New technologies can also lack robust security frameworks, making them vulnerable to exploitation. When these technologies are implemented without proper security measures, cybercriminals can exploit these weaknesses to gain unauthorized access, disrupt services, or steal business information like customer data, financial records, and intellectual property. The increasing connectivity of devices through the Internet of Things (IoT) can also exacerbate these security risks, as each connected device, such as a smartphone, can serve as a potential entry point for attackers. Additionally, dispersed workforces can create additional attack vectors.
These technological challenges reinforce the importance of cybersecurity and the need to reevaluate security postures regularly. Emphasizing integrating risk assessment, risk mitigation, and building resilient systems during this transformation phase should be a priority for small businesses and enterprise organizations.
The vital role of data security in the digital era
Quintillions of bytes of data are constantly created and stored in data centers on-premises or in the cloud daily. The more you refine data, the more effective it becomes to determine the cause of a problem. Data plays a significant role in driving the world and is like the new gold standard, and as such should be treated with as much significance.
Data breaches are also rising since data is used to measure various business activities. Whether a data breach will occur is no longer if but when. Additionally, the common assumption is a breach happens only by an outsider attack is no longer valid. Data breaches can occur by accident, malicious insiders, criminal hackers, and stolen credentials. While internal and external sources can be challenging to prevent and detect, the inability to protect business data against unauthorized access, theft, or manipulation can lead to severe consequences for organizations.
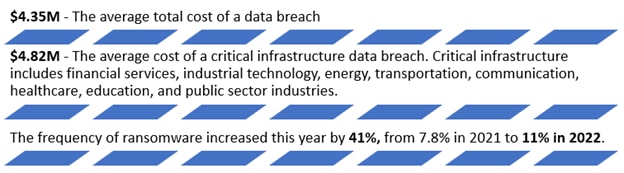
Here are some key statistics about the cost of data breaches, as showcased in the
2022 Ponemon research report from IBM:
Top 3 reasons to revisit your cybersecurity measures today
Ensuring you have effective cybersecurity measures is crucial for both individuals to protect their sensitive information and organizations to prevent data breaches and other cybercrimes by helping safeguard this valuable data.
However, it can be challenging to determine if your current security practices are enough. Here are three common indications your cybersecurity measures may not be sufficient:
- Increased frequency of security incidents: Any security incident, whether a data breach, unauthorized access attempt, denial-of-service attack, or malware infection like Trojans and spyware, can indicate potential vulnerabilities and provide an opportunity to evaluate and strengthen your defenses. With today’s increasing threat landscape, the frequency and volume of attacks, both large and small, are on the rise. Organizations can help address any inadequacies and ensure a more robust and effective cybersecurity posture by consulting cybersecurity experts, conducting security audits, and performing penetration testing.
- Lack of employee awareness and training: Human error can also play a significant role in cybersecurity breaches. Lack of awareness, inadequate training, and risky online behaviors among employees can increase the chances of successful cyberattacks. For instance, social engineering scams can be built to exploit personal details from social media to launch phishing attacks, granting hackers access to social security numbers, bank account details, and sensitive data like health-related information. Insufficient cybersecurity awareness and training underscore the importance of enhanced risk management, including comprehensive training programs and regular awareness campaigns.
- Outdated or missing security software: If your security software, such as antivirus programs, firewalls, or intrusion detection systems, is outdated or missing, it can leave your environment vulnerable. Regularly updating and maintaining security systems is crucial to protecting against evolving threats. Failure to do so can indicate inadequate cybersecurity measures. It is also crucial to evaluate whether your existing cybersecurity solution provides the insights you need into the overall network security, cloud security, and health of your environment.
Why having the right cybersecurity solution is important now more than ever
While various tools and technologies can support different types of cybersecurity measures, such as firewalls, antivirus software, encryption, authentication, backup systems, threat intelligence, policies, and regulations, these individual solutions often can miss the intricacies and dependencies needed to support constant alertness, adaptation, and real-time observability across all environments. By implementing modern cybersecurity solutions, organizations can more easily fortify their defenses, protect business data, and ensure the integrity and availability of critical systems in the face of evolving cyber threats.
SolarWinds
® security solutions can help IT and security teams prevent, detect, and respond to infrastructure, network, systems, applications, and data threats. Our security solutions are built to improve the agility, flexibility, and effectiveness of IT security and compliance teams with the ability to automate compliance reporting and quickly respond to threats. SolarWinds security solutions can help teams increase productivity while keeping security costs and complexity in check, from managing access rights across the infrastructure to actively monitoring suspicious activity.









